Part 2: DeFi Madness ft Curve, iEarn & Stable-Coin Whales
A special edition of DeFi Weekly covering a highly sophisticated DeFi exploit attempt.
Continuing part 1…
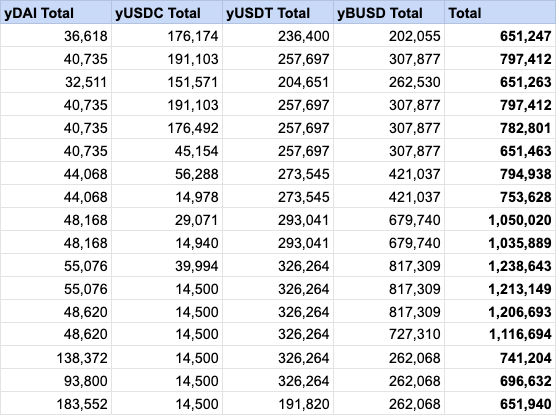
Tx 13:
While we have Charlie doing odd transactions and having lost over $550k, we now have a new user who decides to join the madness - introducing Billy (0x818). Till date, we're still unsure if Billy was malicious, not intelligent or someone who got excited & panicked. His first move is to remove the some yDAI liquidity directly from the pool which nets him a loss of about ~$7,000 since he redeemed 14k shares for $6k of DAI. Anyways, let's keep following through.

New total:

Tx 14:
Billy's second trade is a better outcome for him. He decides to redeem 33k shares for BUSD, however this time he receives $90k BUSD - a net profit of 168%! This is because he's doing the same thing Charlie's doing but in reverse. Explained:
His 33k shares represent a percentage of the entire pool
By redeeming his shares he gets a proportionate amount of each currency ($8.25k each)
He then trades this $8.25k (which the pool gave him) for BUSD
Since USDC and DAI are heavily out of balance, the pool rewards him for his "contribution" which nets him with $90k ultimately!

New total:

Tx 15:
Within the very short time span these trades are going on, Andre and Michael are alerted that someone's losing a large amount of money executing these trades. Their initial reaction is that some clueless trader is losing money and they need to help make them whole. They tap into their contacts and ask a large whale friend to essentially swap 89k worth of DAI for 465k BUSD. On paper this books them a profit of $375k to return to what they think is a clueless trader. Important note that this is the transaction Crypto Twitter was going crazy about (scroll up), little did anyone know this was a white-hat attack to protect a user

New total:

Tx 16:
The next step is why I'm confused by Billy, he decides to withdraw 44k DAI with 89k Curve shares netting him a 50% loss and resulting his final P&L balance to be just over $5k. I find this behaviour strange as he could have far more money doing what Andre and Michael did in the trade above, unless his intention was to withdraw this DAI and then exchange it with BUSD as demonstrated in tx 15. It's too hard to tell but the reality of the situation here is that there were 3 parties, 2 of which had unclear intentions, all interacting with the same contract trying to alter each other's expected outcome! He also does this from an address with an ENS name attached to it, doxxing himself in the process. Good job Billy.

New total:

Tx 17:
During this incredibly short time span, our friendly whale executes the final trade of exchanging 90k DAI for 134k USDT resulting in a net profit of 49%. This ensures that the money lost by Charlie can be recouped (since he's a clueless user, right?)

New total
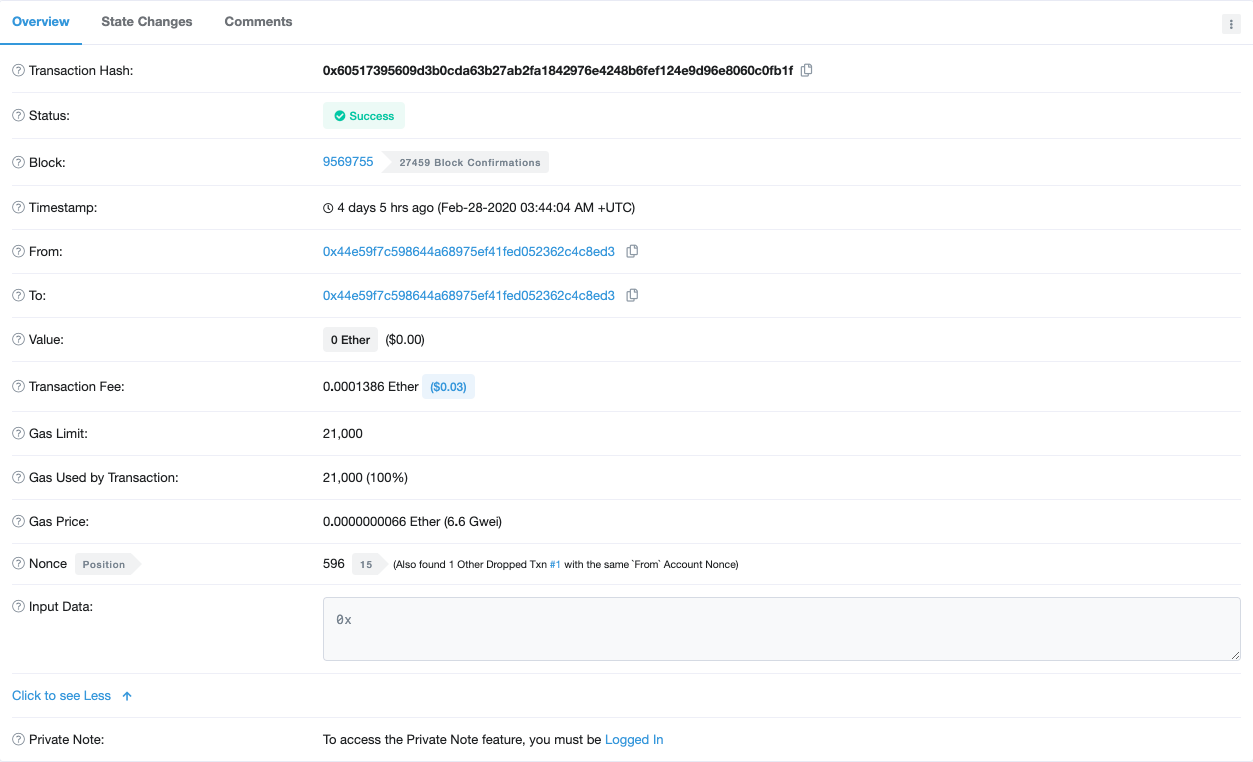
Tx 18:
Charlie, who is oblivious to how he's 3 transactions late to making $250k, makes a final transaction but then realises he lost out on making a killing so cancels it instead! You can see this over here at: https://etherscan.io/tx/0x60517395609d3b0cda63b27ab2fa1842976e4248b6fef124e9d96e8060c0fb1f
This leaves him in an awkward position since he's spent over $700k in attempting this profit scheme, only to be late to the party. It's funny since the ideal way to execute an attack like this would be to write a smart contract and execute it atomically, however he didn't have the technical know-how and lost plenty of money. His next step is to contact Andre and claim that iEarn/Curve messed up and he lost funds and social engineer his way to getting his money back.
Recap
From all of the above, we could probably summarise the situation as follows:
Someone was snooping Github and realised new contracts with fresh liquidity has been seeded
Through this, Charlie (a whale) thinks he can manually manipulate the pools to steal the BUSD and USDT that was seeded
As he's manually executing each transaction, Andre and Michael realise something's not right here
At the same time, Billy also realises something isn't right. He tries to turn it to his advantage but does it with a tiny bit of success. It's still unclear what his intentions were.
Being one step ahead, 'Friendly Whale' execute the trade the 'Malicious Whale' was trying to do (taking out BUSD/USDT at a highly favourable/manipulated price). A few minutes late and they would have lost funds to the tune of $200k+
Charlie, realises the mistake he's made, cancels his supposed master move transaction and is down $500k.
Andre's spent a few days doing a deeper analysis on the various situations, You can check out his spreadsheets with more resolution here:
https://docs.google.com/spreadsheets/d/11aFUTjzHw2F4MsI-Mlzd3gowr4PonSd7PoIa0TFkwMY/edit#gid=0
Here's each player's final outcome and transaction log history.
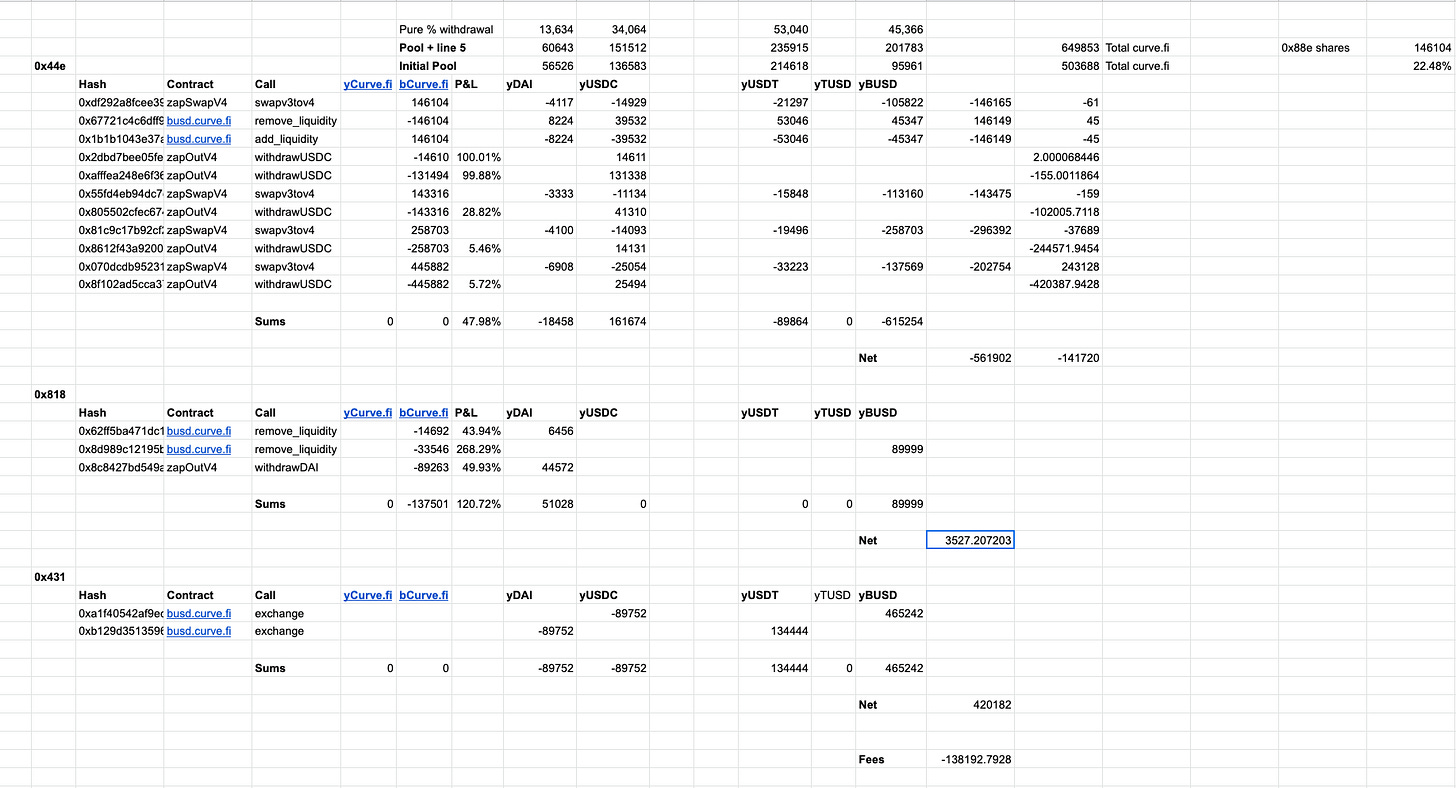
Expected profit analysis:

Looking Back
Now that everyone's hopefully on the same page about what happened, I'd like to spend some time about the aftermath and the non-financial loss that happened.
Firstly, gathering and analysing the above data has taken close to 4 days (full-time) by Andre and can only be analysed with someone who has specialised knowledge in this field. It's taken me alone 2-3 days to wrap my head this all and explaining it in a way to give true insight to people about what's happened. However, many people in the community failed to take this into consideration and started a witch hunt against Andre (for something he wasn't directly responsible for and does for free).
Furthermore, many people had expectations such as the following:

@Chis, I appreciate the work you do for DeFi. Please do not take this as a personal attack.
Through all of these events Andre's decided to stop working on iEarn.


I personally find this really disappointing. It's not that people shouldn't expect a response, but community members and those with influence should be patient and give time for the devs to create a thorough report of what actually went down. Andre released an initial post mortem after 24 hours over here: https://gist.github.com/andrecronje/decacace45d41dd0c6de11ea1d6d6b57
As you can probably see from the above, it's far less detailed than this one: https://docs.google.com/spreadsheets/d/11aFUTjzHw2F4MsI-Mlzd3gowr4PonSd7PoIa0TFkwMY/edit#gid=0
24 hours is not enough to analyse complex on-chain attacks and those who have the understanding to decode it need to be given at least 1 week to figure out what exactly went down and discover preventative measures to ensure it doesn't happen.
I'm more than happy to help the community understand complex attacks such as these and work closely with teams, although I request everyone reading here to just be a little more patient. We're all humans trying our best to create a new financial system.
Calling people out with incomplete information isn't holding people accountable but rather destroying the community from within.
Unanswered Questions:
Alright, now that I've covered majority of what I wanted to, I still have some unanswered questions that I'd love to hear a response from you all from via email replies or Twitter.
Should 0x44e59f7c598644a68975ef41fed052362c4c8ed3 (Charlie) get his money back when his on-chain transaction history clearly showed he was trying to drain the USDC pool and use it to execute a more profitable swap? The friendly whale still holds the $500k from the white hack recovery.
What were 0x8183866223445441b6fb9206b9f0b583410977e6's (Billy) intentions? When his identity was uncovered (ENS name) why did he run away and delete himself off the face of the planet if he only made $3k?
Who is really at fault here? Open source developers or users poking around un-official technology trying to exploit it for their own benefit?
I'm personally fascinated with this whole incident and find it amazing the level of sophistication we've reached in such a short period of time with this stuff.
Learnings and Future Exploits
Devs, don't rush. Tell people you need a week to get back to give a complete break down. Inform of timelines but don't scramble to give answers. This is completely reasonable. Don't rush to restart.
Users, wait until technical community members or audit companies can fully articulate what happened. Shouting and accusing people doesn't help and only increases the chance of further mess ups.
Assume everything on-chain is being watched and as soon you post an address to Github (via migration JSON files or other methods), be careful.
Attackers, if you're going to do an attack, please don't be stupid and do it as individual transactions lol.
Using DeFi is risky, don't invest large amounts of money unless you've done thorough due diligence (technical and economic analysis required).
Closing
I've really enjoyed writing this piece and hope you found value from this. A lot of data gathered here was through the help of Andre and I'd like to thank him for this time and also dedication to being a builder in this space. I think we all owe it to him for being as transparent as possible while doing this for close to 0 benefit.
Have to say though, I'm amused by community's desire for more in-depth analysis of complex technical matters like these. Thank you for being such amazing readers.
If you found this useful, please let me via email or Twitter (@kermankohli) - I'd love to hear from you.
